The K-12 STEM Center follows all University guidelines for protecting students, families, teachers, and staff during the COVID-19 pandemic and USC reopening attempts. Learn More.
K-12 STEM Center & Cybersecurity
The K-12 STEM Center provides Viterbi students to serve as technical mentors to high school teams participating in CyberPatriot. CyberPatriot is the Air Force Association’s national youth cyber education program designed to excite, educate, and motivate the next generation of cyber defenders critical to our nation’s future security. The program features the National Youth Cyber Defense Competition, a tournament-style competition in which high school and middle school students compete to defend a computer network against attack in a series of web-based competition rounds.
The K-12 STEM Center also offers an online Cybersecurity Course for high school students. To learn more about the course please click here.

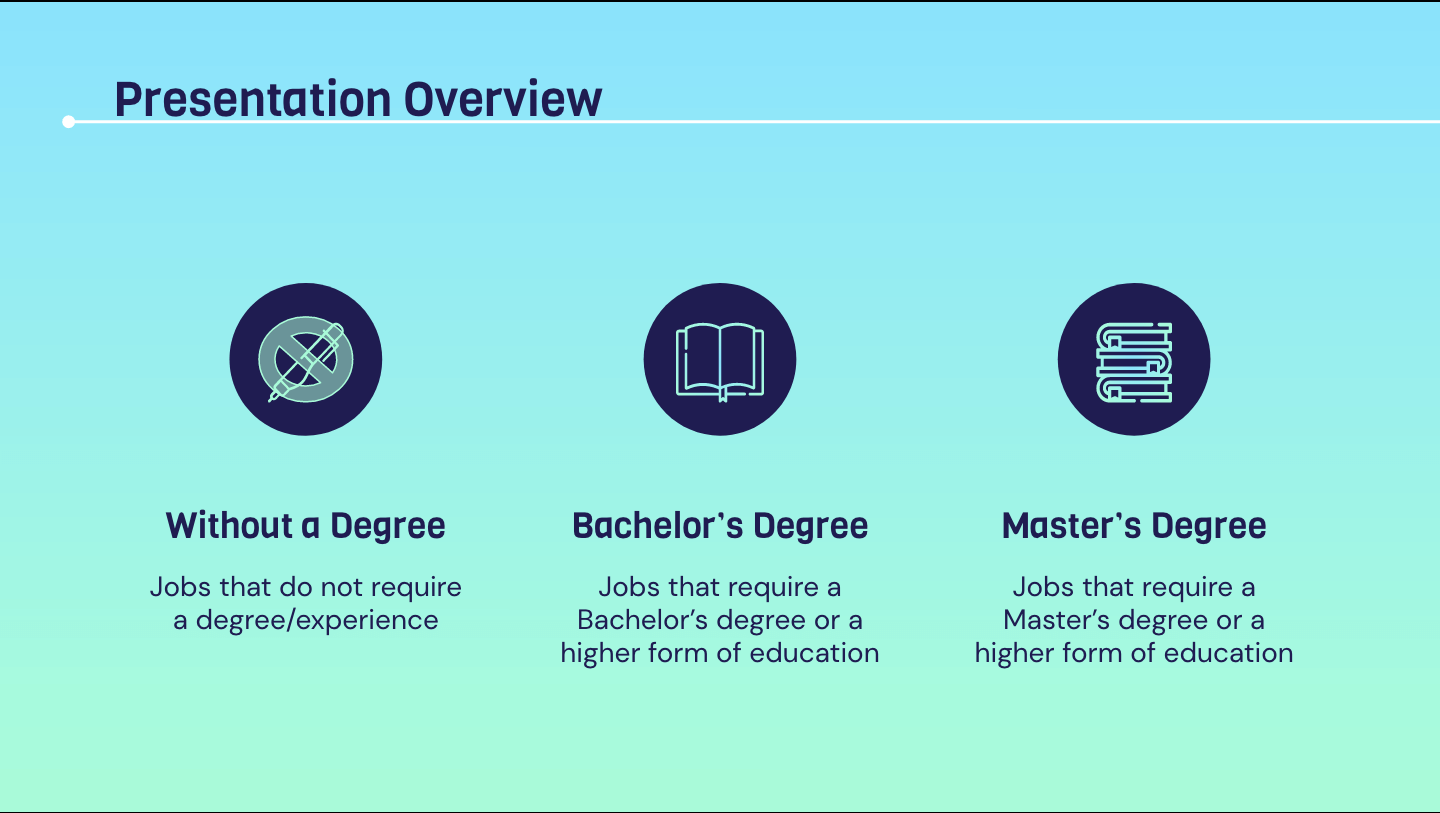
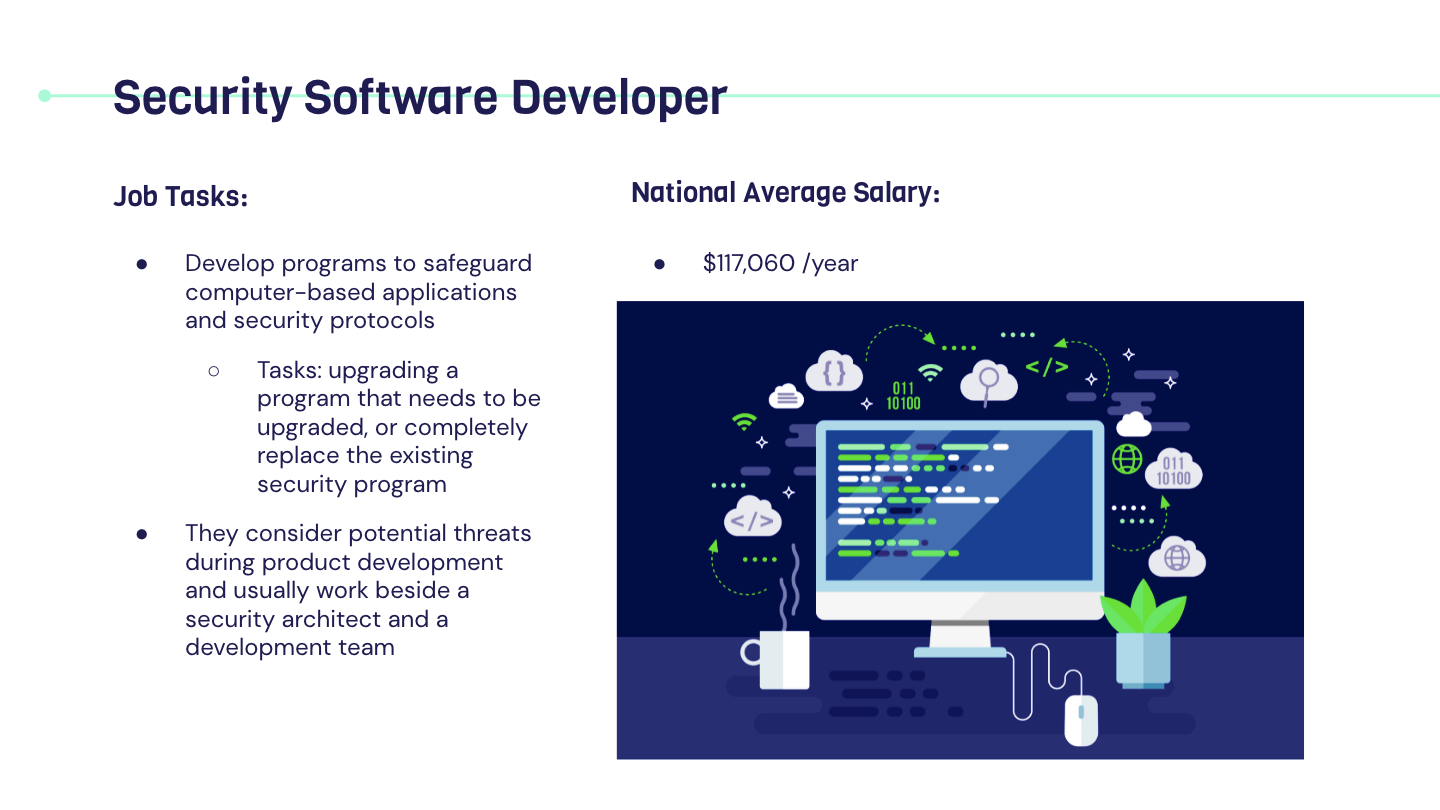
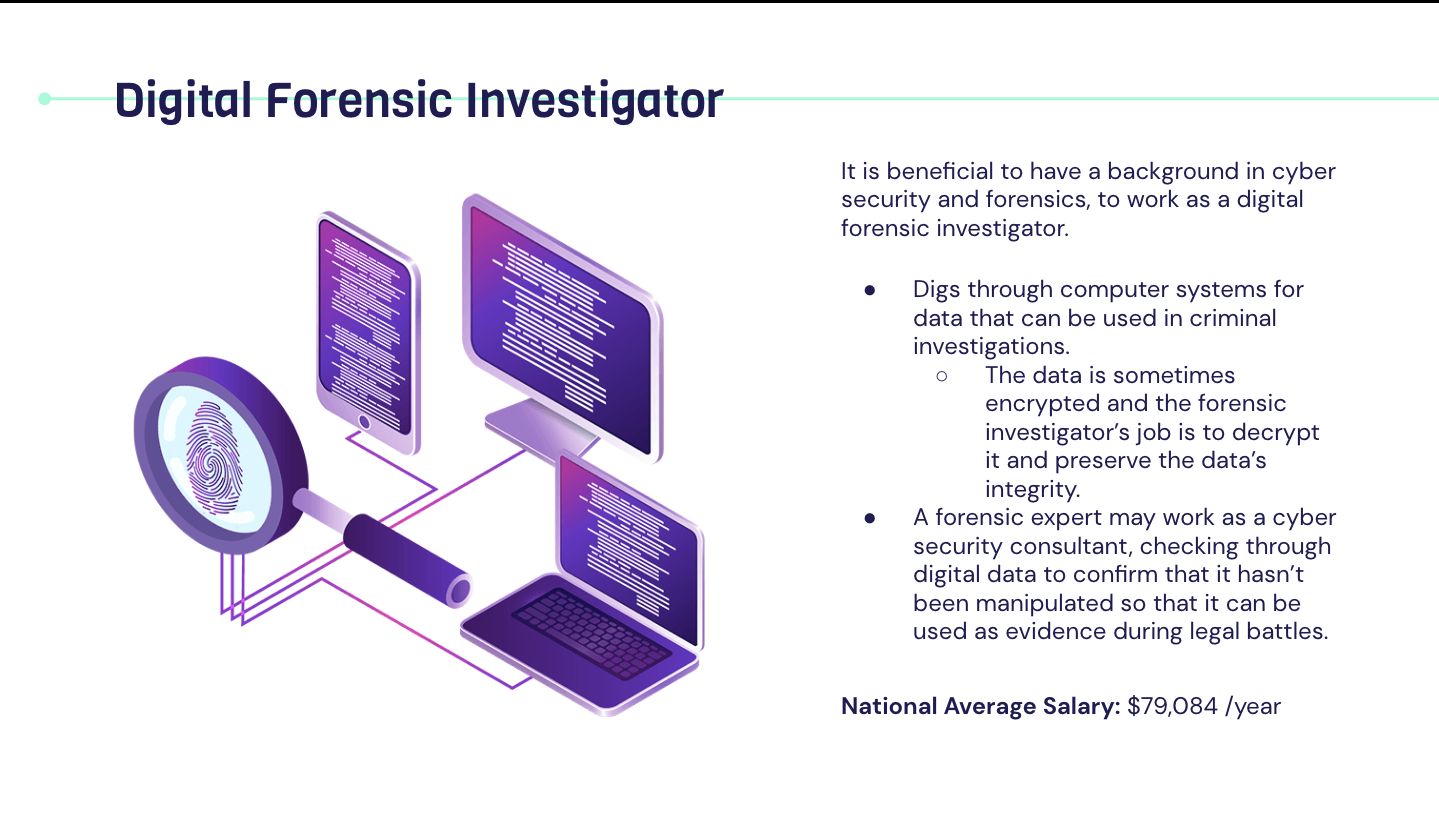
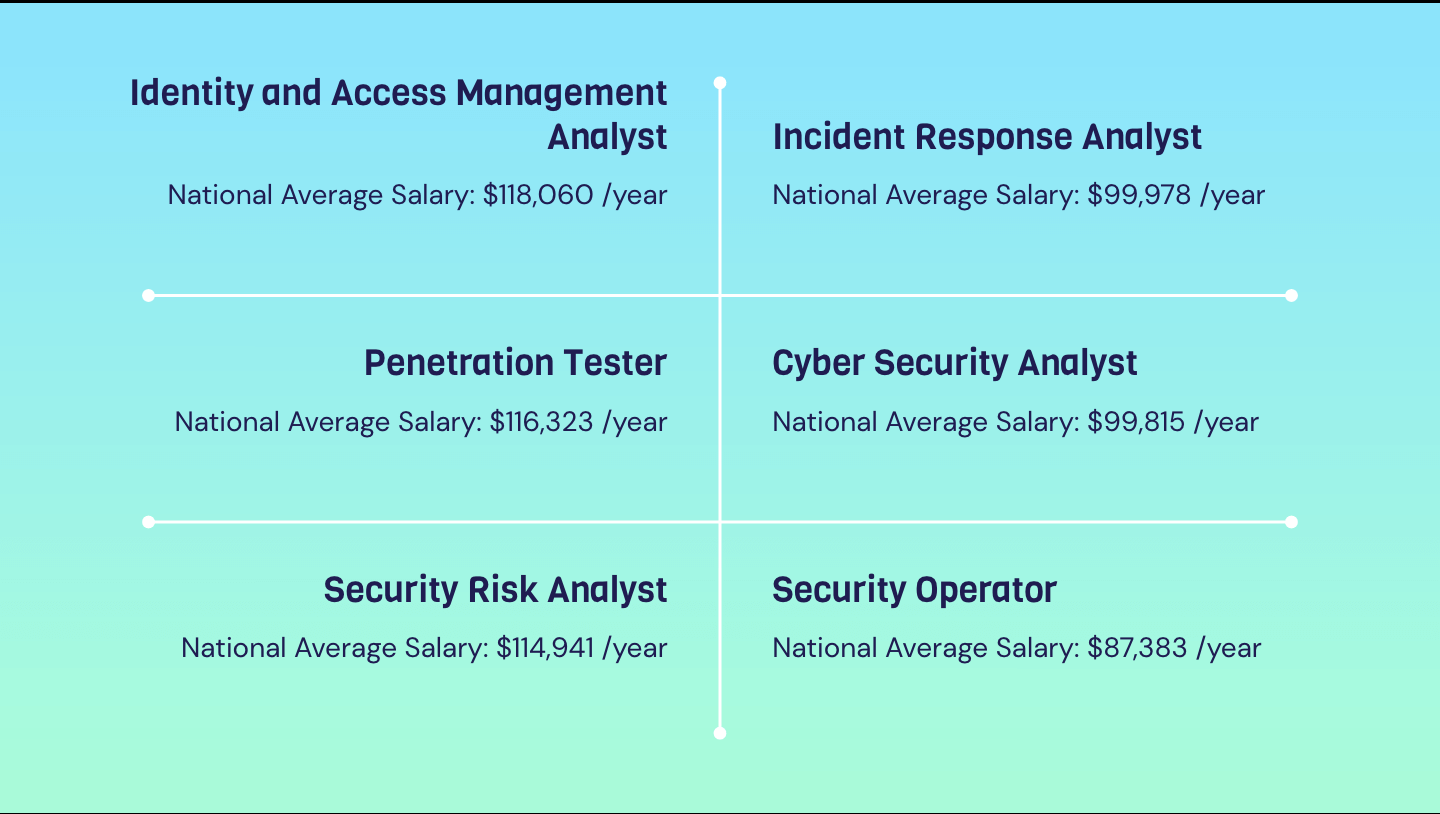
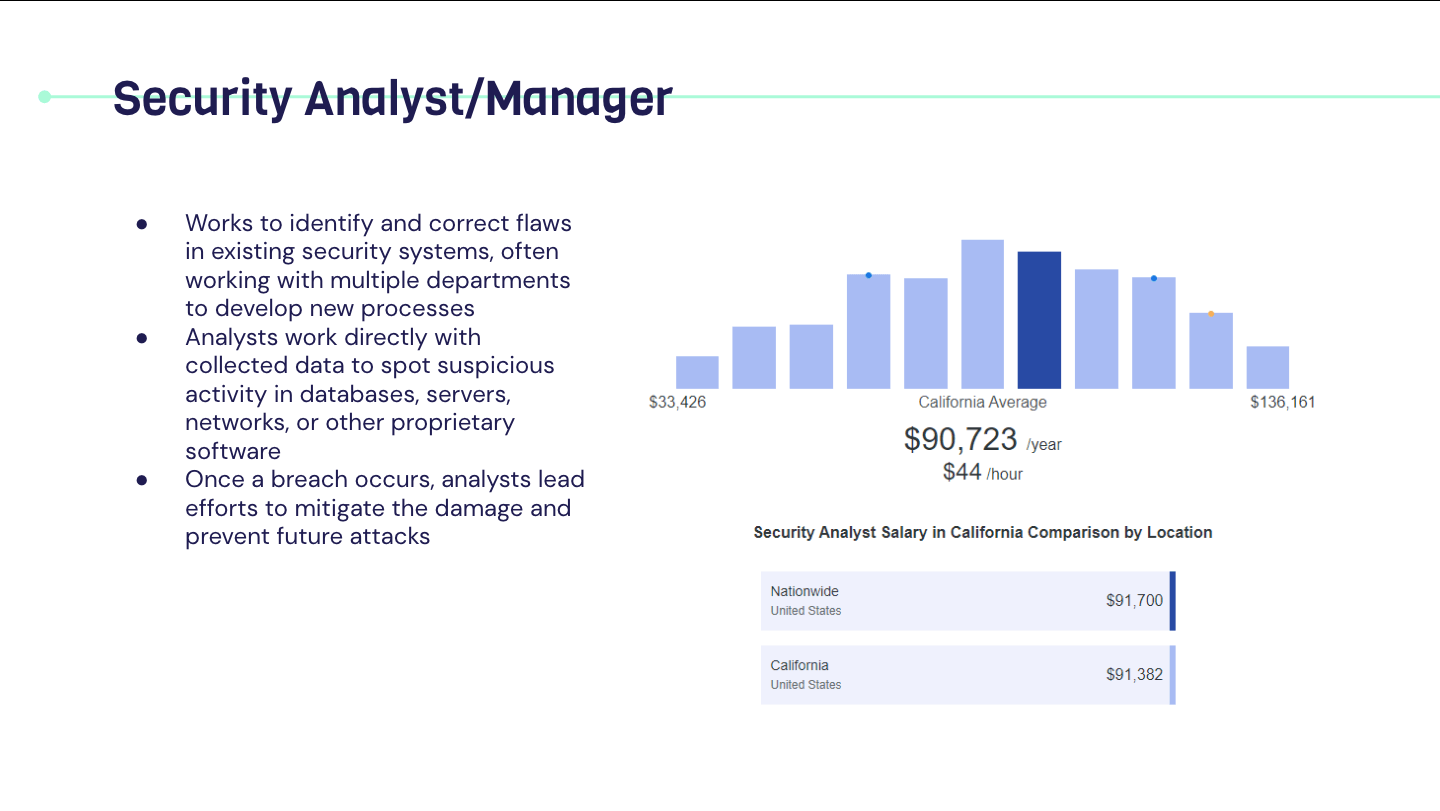
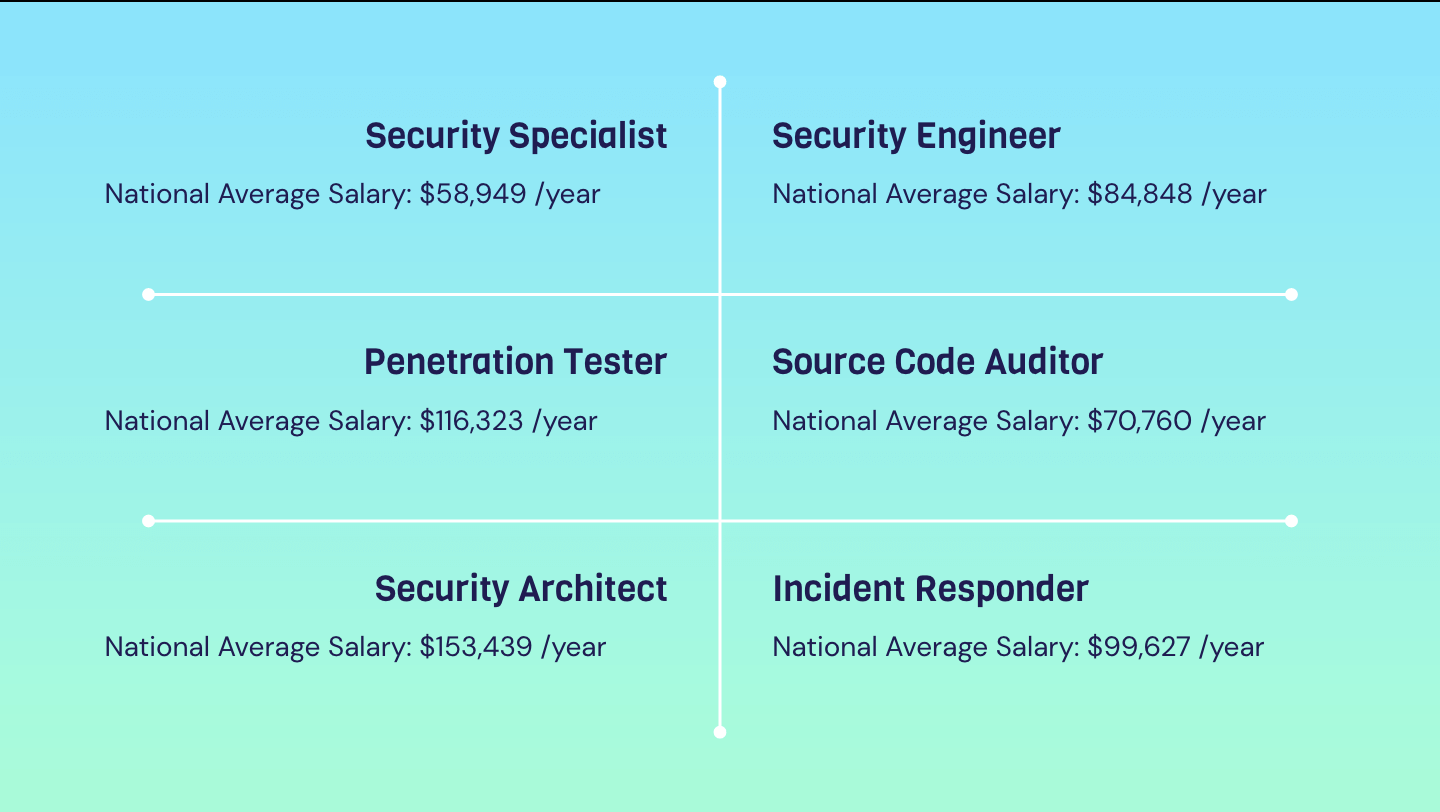
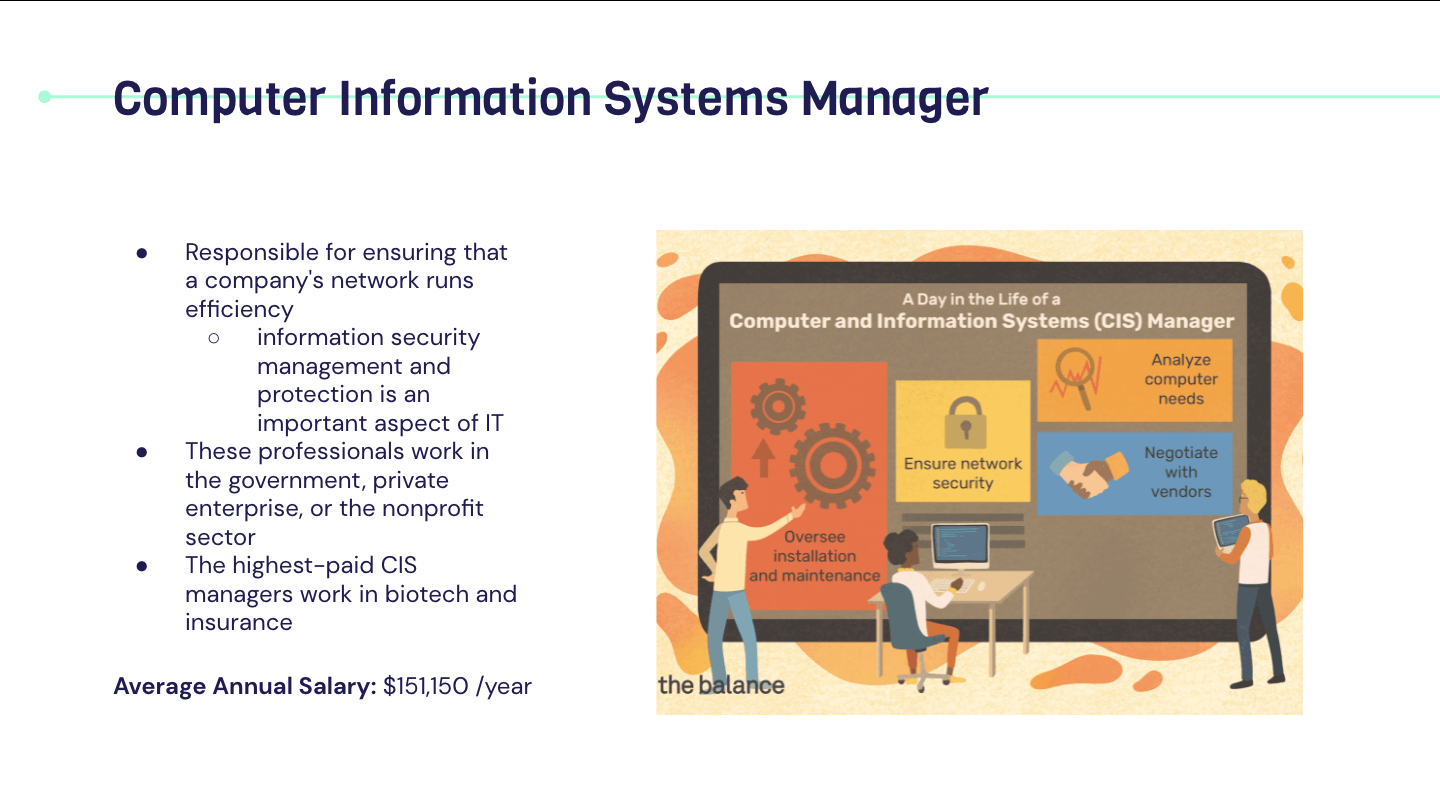
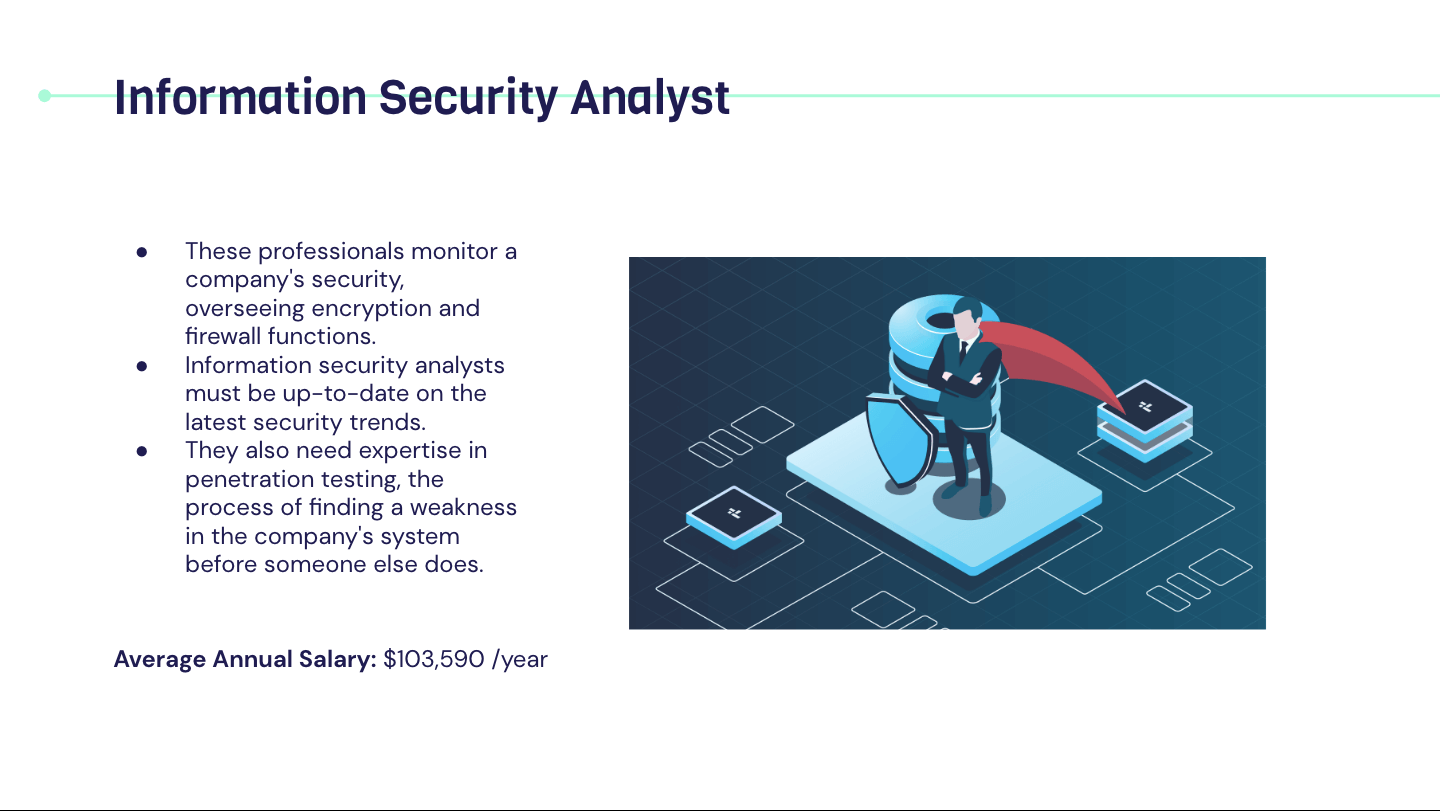
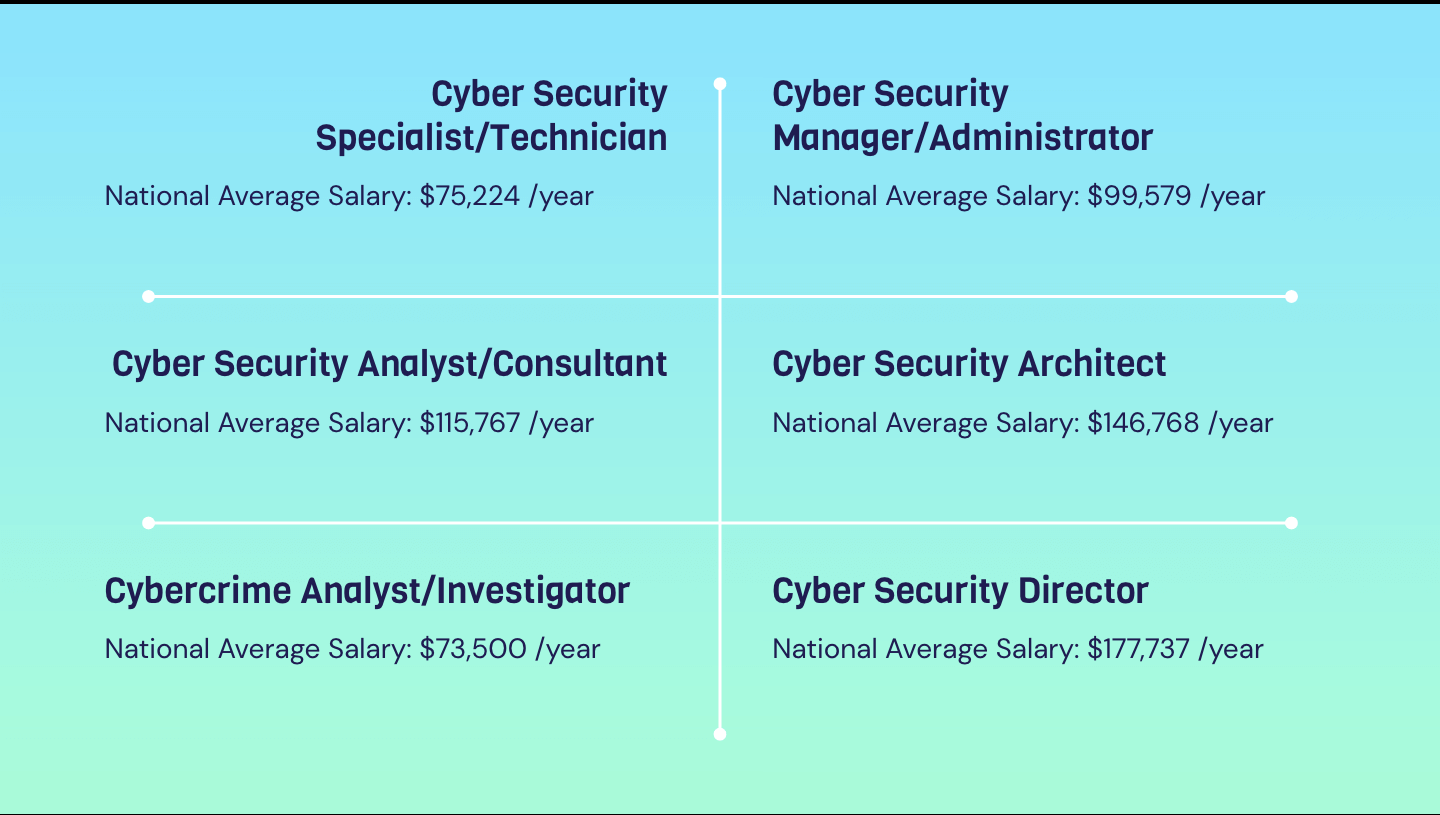
Career In Cyber Security
Cybersecurity and You
Social Engineering
Phishing
Passwords
Zero Day Attacks
IOT hacking
Free wifi hacking
Resources
FBI’s Safe Online Surfing
Educate & Entertain students on ways to stay safe on internet by playing games
Public Broadcasting Service
Offers a library of resources for kids that want to explore cybersecurity.
NJCCIC E Learning For Kids
Encourages students to learn and explore by providing articles & games
KnowBe4 Children’s Cybersecurity Activity Kit
Offers free activities & videos to teach younger kids about cybersecurity.

Learn Kali Linux
Kali Linux tutorial covers both fundamental and advanced hacking and penetration testing concepts. The following Kali Linux tutorials are designed for both beginners and professionals:
Check out the video tutorials!
Published on February 2nd, 2022
Last updated on September 6th, 2022